Application Onboarding for Modern IGA
Smart Automation for Faster IGA Delivery, Consistent Authorization Data, and Built-in Governance from Day One.
Why Traditional Application Onboarding Fails in Modern IAM
Application onboarding is still dominated by manual work. IAM teams, system integrators, and managed service providers depend on application owners to deliver accurate, complete access information, but the data is scattered, outdated, or locked in silos.
Collecting entitlement lists, technical details, system attributes, and role information consumes weeks. Spreadsheets and wikis introduce errors, creating rework and delaying go-lives.
In regulated industries the stakes are higher. Frameworks like DORA, BAIT, VAIT, SOX, and GDPR expect complete, current, and audit-ready documentation, including IAM Governance Docs as part of the overall access model. Most organizations lack a structured onboarding process to meet these demands reliably.
From Fragmentation to Flow: Structured Application Onboarding with NEXIS 4
NEXIS 4 transforms application onboarding into a clear, AI-supported workflow. All relevant information from application owners, IT teams, and existing documentation is consolidated, validated, and structured in one place. The defined access model flows directly into the IGA platform.
Core Capabilities for Scalable, Compliant Application Onboarding
AI-Supported Information Gathering
Upload specifications, user stories, or Confluence pages. AI extracts entitlement data, ownership, access paths, and technical details. Application owners validate instead of rebuilding information manually.
Template-Based IAM Governance Docs
Standardized templates capture business context, entitlement catalogs, criticality, SoD constraints, and regulatory attributes. Complexity adapts to each application, from simple SaaS tools to high-risk core systems.
Integrated SoD and Risk Controls
SoD rules and risk criteria apply automatically. Toxic combinations, excessive entitlements, and high-risk patterns are detected early.
NICO - NEXIS Intelligent Co-Pilot
NICO guides application owners and IAM teams with anomaly detection and clear recommendations. Peer-group comparison improves quality and consistency across the application portfolio.
End-to-End Integration with IGA
Approved access models such as roles, entitlements, and attributes flow directly into the IGA platform. Updates follow governed workflows and recertification cycles.
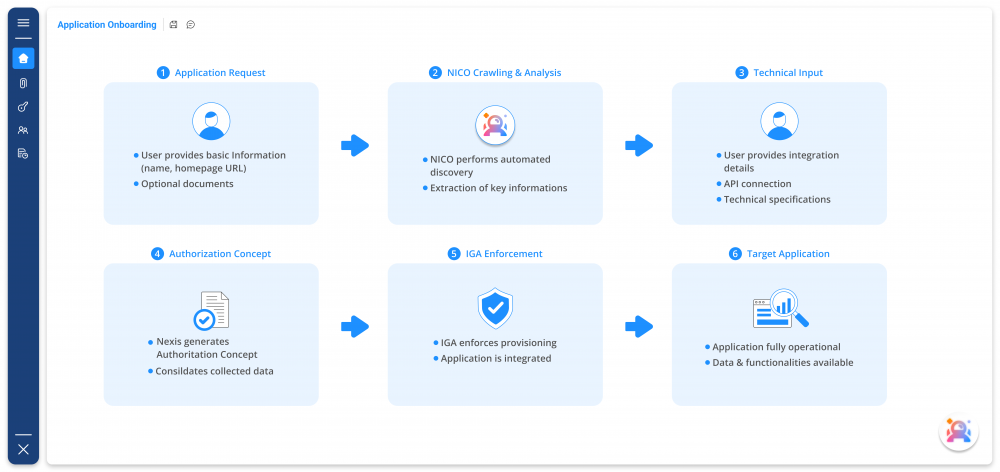
From Documentation to Deployment – A Structured Onboarding Workflow
Every version remains audit-ready, including historic snapshots that show how access changed over time.
Discover and Collect
- Import application information and existing documents
- Auto-detect identity and entitlement data from connected systems
- Classify the application by criticality and regulatory scope
Model and Validate
- Generate a structured IAM Governance Doc based on templates
- Enrich with live data such as roles, entitlements, SoD rules, and metadata
- Run AI-based quality checks, SoD analysis, and risk scoring
Publish and Integrate
- Approve with owners, security, IT, and compliance
- Push access models into the IGA system
- Activate ongoing validation, drift detection, and recertification
Built-in Compliance and Audit-Ready Documentation – From Day One
NEXIS 4 embeds compliance requirements directly into onboarding:
- Alignment with DORA, BAIT, VAIT, GDPR, SOX and related frameworks
- Centrally managed templates, always consistent and up-to-date
- Full lifecycle tracking from draft to approved concept
- Versioning, PDF export, and historic reconstruction for audits
- Continuous comparison between designed and actual entitlements
Who Gains the Most From Automated Application Onboarding?
IAM and IGA Teams
CISOs & Security Architects
Compliance & Audit Functions
Application Owners









Your Personal Webdemo
Get to know NEXIS in action!
Let us guide you through the software in a no-obligation session and explore its full potential for your business.
Here’s what to expect from your personal NEXIS web demo: