Identity Analytics That Makes Access Risk Visible
Turn Fragmented Identity Data into Insight, Control, and Audit-ready Decisions
From Data Silos to Identity Intelligence
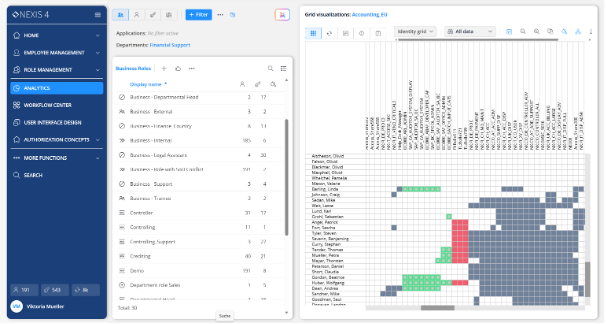
Identity data in large organizations is often fragmented across IGA systems, PAM tools, and business applications. As an Identity Visibility and Intelligence Platform (IVIP), NEXIS consolidates access data across your IAM stack into a single, analytics-driven layer. The result: unified identity analytics that make access risks visible, role models explainable, and compliance decisions traceable.
With AI-powered detection, intuitive visualizations, and governance-ready documentation, NEXIS enables security, risk, and IAM teams to stay in control.
Time Based Access Visualization: Visualize Access Over Time – Not Just in Snapshots
Access risk isn’t static. Authorizations change as roles evolve, people move, and systems grow. NEXIS brings time-based visibility to your identity data, so you can understand not just who had access, but when and why. And the best: It’s the same exceptional user experience whether it’s current data or data from the past.
By consolidating entitlements from across IGA, PAM and business systems, NEXIS gives you a 360° view of access at any point in time.
Risk Scoring & Anomaly Detection: Making Identity Risk Visible, Measurable and Actionable
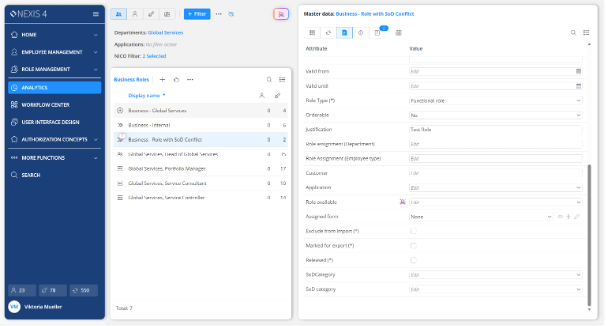
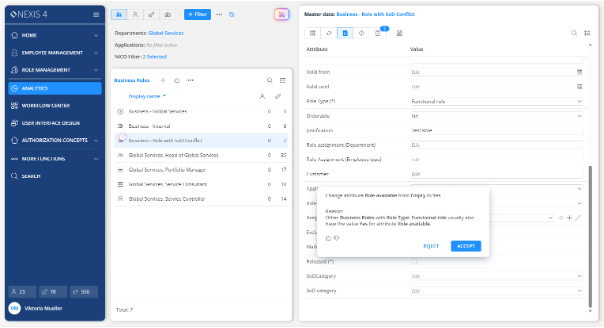
NEXIS uses explainable AI to detect anomalies in identity data and highlight critical risks across IGA, PAM and business systems. Risk scoring and posture management are based on actual usage, authorization structures and policy violations, enabling targeted risk reduction.
Cross-system analytics reveal toxic combinations and SoD violations that may span administrative and business roles, including those that often remain hidden in individual systems.
Reports and Policy Insights: From Analytics to Actionable Policy Insight
Identity Analytics in NEXIS delivers more than raw data. Configurable dashboards, structured reporting and policy-linked metrics translate analysis into operational and audit-ready insight.
Policy definitions, recertification activities and SoD monitoring are consistently linked to actual authorization data, enabling traceability and alignment across systems.
Policy insights commonly surfaced through NEXIS:
- Roles and systems with high SoD conflict density
- Business units showing excessive privilege accumulation
- Recertification campaigns with high acceptance or rejection or escalation rates
Historical Access Evolution: Versioned Access History for Audit and Compliance
In regulated environments, understanding how access has changed over time is as critical as knowing the current state. NEXIS 4 treats historical access evolution as a core capability to support forensic analysis and audit transparency.
All changes to IAM Governance Docs, role structures and entitlement catalogs are versioned and time-stamped, including release approvals and documentation steps.
Forensic and compliance-relevant insights include:
- SoD rules active at the time of specific transactions
- Historical role assignments and account holders at any point in time
- Timeframes and systems involved in risk remediation efforts
These Companies Rely on NEXIS









Your Personal Webdemo
Get to know NEXIS in action!
Let us guide you through the software in a no-obligation session and explore its full potential for your business.
Here’s what to expect from your personal NEXIS web demo: