Real-Time Identity Risk Detection with NEXIS ISPM
Detect Identity Threats Before They Become Incidents: NEXIS ISPM Reveals Critical Identity Risks that IAM Alone Can’t See
Close the Gaps in Your IAM with ISPM
Digital identities are the new attack surface. NEXIS ISPM (Identity Security Posture Management) helps you detect unusual access, hidden risks, and misassignments – in real time.
Common identity risks include:
- Anomalies and deviation from historic identity data
- Orphaned or inactive privileged accounts
- Redundant access rights blocking revocation workflows
- Entitlements assigned outside of working hours
- SoD violations across fragmented systems
- Misassignments caused by identical names
These issues are often invisible to traditional IAM systems – until it’s too late. NEXIS ISPM fills that gap with proactive monitoring and intelligent, automated response.
Stronger Identity Security Starts with ISPM
Real-time Transparency
Smarter Compliance
Faster Response
Cleaner Entitlements
Stronger Posture
Lower Operational Overhead
How NEXIS ISPM Detects and Resolves Identity Risks in Real Time
NEXIS ISPM's capability leverages AI-driven methodologies to detect, evaluate, and resolve security vulnerabilities in real time and at admin time.
Using sideloads and NEXIS identity data, ISPM continuously ingests and correlates identity data, enabling near real-time insights into identity-based threats. This allows organizations to detect and react to anomalies before they escalate.
ISPM maintains continuous policy enforcement and ensures compliance with standards like GDPR, DORA, and NIS2 – with full audit documentation and versioning.
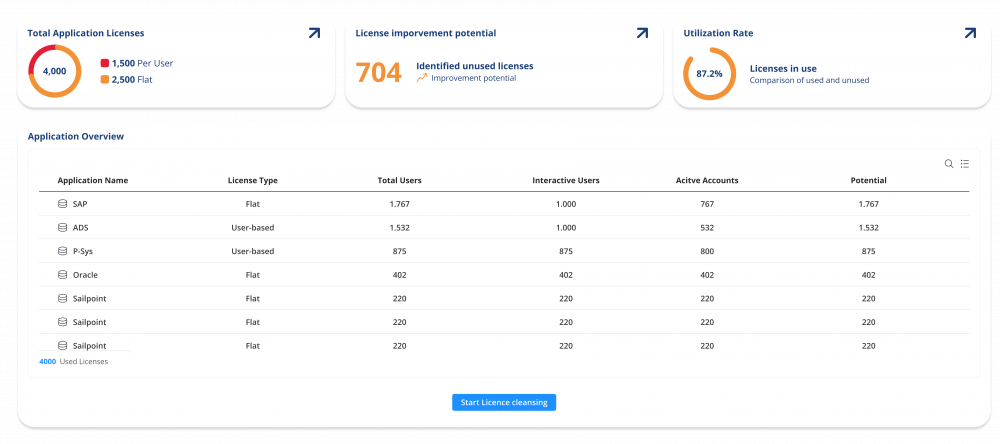
The License Killer: License Optimization as a Built-In ISPM Capability
The License Killer extends NEXIS ISPM with targeted insights into license and authorization usage. It helps organizations reduce costs, eliminate unused access, and align entitlements with actual usage.
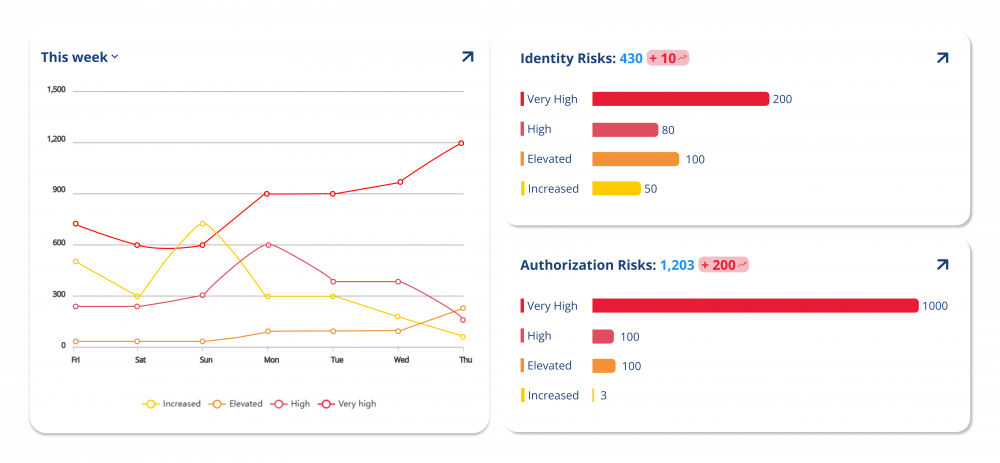
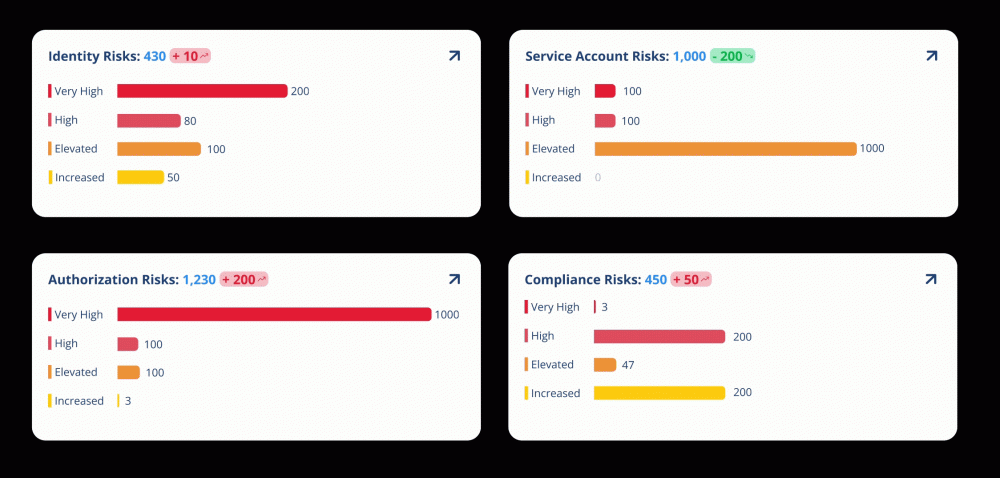
Risk and Compliance Dashboards: Shared Identity Intelligence for Security, Compliance and Governance Teams
NEXIS enables dashboards that surface identity-related risks, policy gaps and optimization potential. Built on the Business and Governance reporting layers, these views help align security operations, compliance functions and access owners on a shared set of facts.
Dashboards are configurable by role and responsibility:
- Executives (CISO, CIO, Risk) see security and compliance at a glance
- IAM and SecOps teams track operational workloads and exception trends
- System and application owners gain clarity on authorization status and review obligations
Control Coverage Monitoring: See What’s Covered and What’s Not
Modern IAM landscapes span IGA, PAM, access management, and business systems. NEXIS ISPM's capabilities reveal which identities, accounts and entitlements are actively governed and where control gaps persist.
By turning governance coverage into measurable KPIs, NEXIS adds an observability layer across the identity fabric, enabling audit teams, risk owners and IAM leads to validate not just what is configured, but what is actually controlled.
Your Personal Webdemo
Get to know NEXIS in action!
Let us guide you through the software in a no-obligation session and explore its full potential for your business.
Here’s what to expect from your personal NEXIS web demo: