AI-Powered IAM Governance Docs
Replace Spreadsheets and Static PDFs with AI-supported, Audit-ready Governance Documentation.
From Spreadsheets to Smart Governance
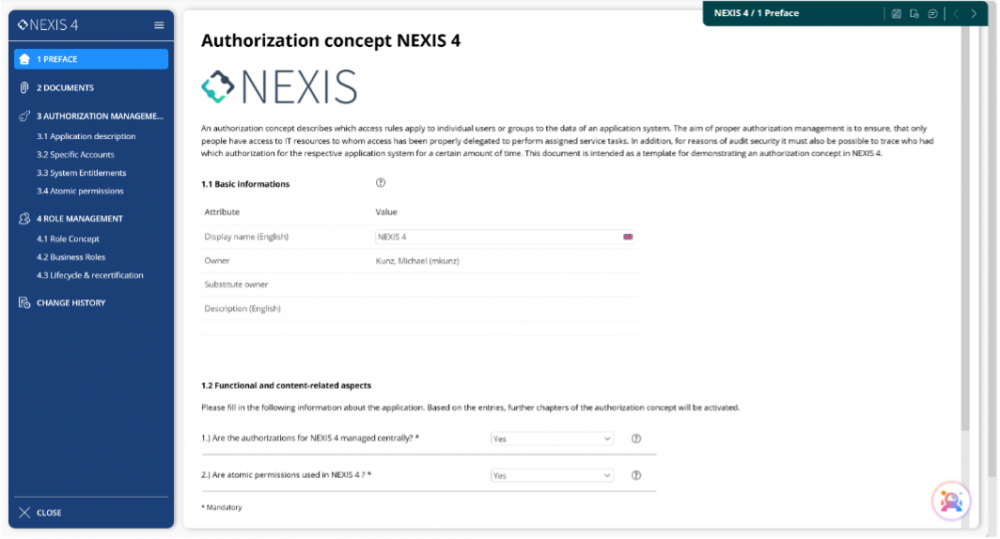
IAM Governance Doc in NEXIS 4 transforms regulatory documentation from a static requirement into a living, operational asset. Instead of managing fragmented Word or Excel files, or Wiki-based appraoches organizations gain a centralized, versioned and policy-driven documentation layer that is directly tied to real-world identity and access data.
Structured templates guide application owners, while integrated AI analyzes existing documents to pre-fill relevant sections and flag inconsistencies in real time. Every concept becomes an active part of your governance strategy – continuously updated and audit-ready.
Each IAM Governance Documentation captures the complete access governance context for an application or service, including:
- Business and technical application details
- Purpose, risk classification and regulatory scope (e.g., DORA, BAIT, VAIT, GDPR, SOX)
- Role structures and entitlement catalogs
- Criticality ratings and SoD constraints
- Review workflows and approval chains
- Connectivity and master data references
Faster creation
Audit-Ready Evidence
Lifecycle Integration
Better Quality
Scalable Governance
Policy Framework: Structured Policy Layer for IAM and Compliance Teams
Central templates define mandatory sections, metadata, control questions and approval steps, aligned with internal policies and regulations such as DORA, BAIT, VAIT and ISO 27001.
Each application receives a risk classification that drives scope and depth of documentation. High risk systems can require extended sections, additional controls or more stringent approval flows.
Segregation of Duties (SoD) rules, toxic combinations and policy constraints are documented. The interactive SoD matrix and policy rules provide a consistent control layer across cloud, SaaS and on-prem systems.
NEXIS 4 extracts relevant information from existing documentation (user stories, specifications, Confluence pages) and pre fills the IAM Governance Doc. Explainable AI validates consistency and supports authors during refinement.
Authorization Catalog: Single Source of Truth for Roles and Entitlements
At the core of each IAM Governance Doc is a structured authorization catalog. NEXIS 4 imports current roles and entitlements from connected IGA systems, PAM and other sources, and pre-fills the catalog with live data. Concept metadata (such as criticality tags) is written back into IGA to keep implementation and documentation in sync.
Control Mapping & Evidence Support: From Governance Text to Audit Ready Evidence
IAM Governance Doc is designed as an evidence engine for audits and internal controls:
Control Mapping
Validation & Drift Detection
Versioning
Reports & Logs
Business roles make our life better - With NEXIS 4 role management we can standardize user access and improve our internal customer experience.

Facilitating Nexis tools and consulting services allowed us to streamline and secure user management processes.
With Nexis consulting services we were able to conceptualize an IdM infrastructure based on our company-specific requirements. Furthermore, Nexis provided valuable support to help us develop a profound strategy for future-proof IAM.

NEXIS successfully allows us to monitor and improve the fulfilment of relevant regulatory requirements. It covers our company-wide compliance and SoD controls and provides a new level of transparency and auditability. It thus is one of the core elements of our security infrastructure.

Your Personal Webdemo
Get to know NEXIS in action!
Let us guide you through the software in a no-obligation session and explore its full potential for your business.
Here’s what to expect from your personal NEXIS web demo: